Security Documentation
Security is at the core of Waddles Bot. We implement multiple layers of protection to ensure your funds and data remain safe at all times.
Encryption System
Our encryption system uses industry-standard protocols to secure your data:
- AES-256 encryption for all sensitive data
- End-to-end encryption for all communications
- Zero knowledge architecture - we never see your private keys
- Encrypted local storage with secure key derivation
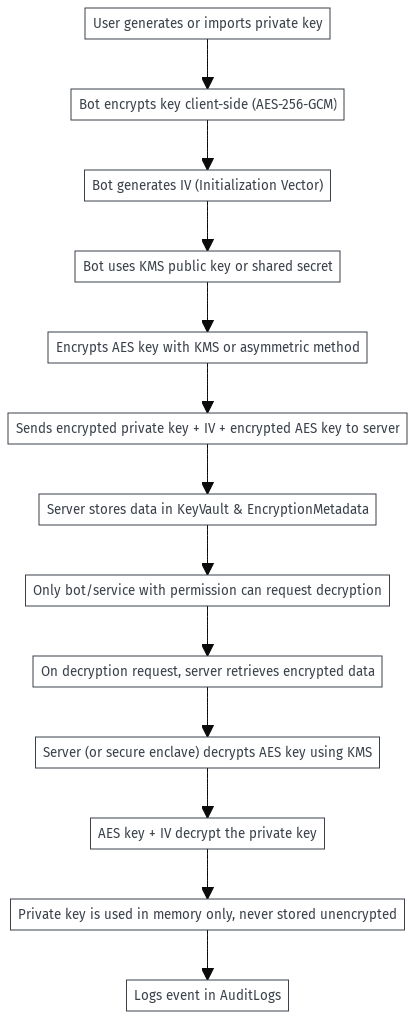
Key Storage Process
When you first set up your wallet:
- You generate or import your private key
- The bot encrypts your key client-side using AES-256-GCM
- A unique Initialization Vector (IV) is generated for enhanced security
- The bot uses a Key Management Service (KMS) with either a public key or shared secret
- Your encrypted private key, IV, and encrypted AES key are securely transmitted to the server
The data is then stored in two separate secure components:
- KeyVault: Stores your encrypted keys
- EncryptionMetadata: Stores the IV and encryption algorithm details
Session Management
Our session management system ensures secure access:
- Automatic session timeouts after periods of inactivity
- Secure session token handling
- Device-specific session tracking
- Immediate session termination capability
Session Security Features
Our comprehensive session management includes:
- Robust authentication of session tokens before any key access
- Detailed session tracking with expiration timestamps
- Complete audit logging of all session activities
- IP address and user agent tracking for security
- Telegram account integration with 2FA support
Secure Data Access
Our secure data access protocols ensure that only authorized users can access sensitive information, with multiple verification layers to prevent unauthorized access.
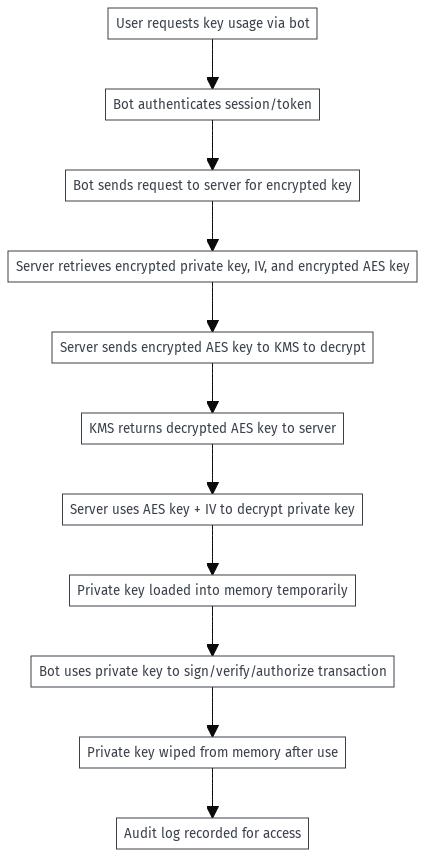
Key Access Process
When you need to use your private key:
- The bot authenticates your session and token
- The server retrieves your encrypted private key, IV, and encrypted AES key
- The encrypted AES key is sent to KMS for secure decryption
- The decrypted AES key and IV are used to decrypt your private key
- Your private key is loaded into memory temporarily
- After use, your private key is immediately wiped from memory
- Every access is logged for security auditing
Security Architecture
Our database architecture implements multiple security layers:
- Separate storage of encryption metadata and encrypted keys
- Comprehensive audit logging of all security operations
- User authentication and session management
- Secure key storage with encrypted backups
- Zero-knowledge architecture ensuring private keys are never exposed
Security Best Practices
Critical Security Guidelines
- Never share your private keys or recovery phrases with anyone
- Enable 2FA on your Telegram account
- Use unique passwords for each wallet
- Regularly verify your active sessions
- Keep your recovery phrases in a secure, offline location
- Always verify transaction details before confirming
- Set reasonable trading limits for each wallet
- Use multiple wallets to distribute risk
- Regularly update your device's operating system and security
- Be cautious of phishing attempts and impersonators